The pinnacle of safety advocacy at Datadog, a cloud-based monitoring and analytics platform, has urged enterprises in Australia and the APAC area to speed up phasing out long-lived credentials for standard hyperscale cloud companies, warning that they continue to be a critical information breach threat.
Talking with TechRepublic, Andrew Krug highlighted findings from Datadog’s State of Cloud Safety 2024 report, which recognized long-lived credentials as a persistent safety threat issue. Whereas credential administration practices are enhancing, Krug famous they aren’t advancing as shortly or successfully as wanted to mitigate dangers.
Lengthy-lived credentials are nonetheless an enormous menace to cloud safety
The report revealed that just about half (46%) of organisations utilizing AWS depend on IAM customers for human entry to cloud environments — a observe Datadog referred to as a type of long-lived credential. This was true even for organisations utilizing centralised id administration to grant entry throughout a number of methods.
Furthermore, almost one in 4 relied solely on IAM customers with out implementing centralised federated authentication. Based on Datadog, this highlights a persistent challenge: whereas centralised id administration is changing into extra frequent, unmanaged customers with long-lived credentials proceed to pose a big safety threat.
 Practically half of organisations utilizing AWS are nonetheless utilizing long-lived credentials. Supply: Datadog
Practically half of organisations utilizing AWS are nonetheless utilizing long-lived credentials. Supply: Datadog
The prevalence of long-lived credentials spans all main cloud suppliers and infrequently contains outdated or unused entry keys. The report discovered that 62% of Google Cloud service accounts, 60% of AWS IAM customers, and 46% of Microsoft Entra ID purposes had entry keys that had been greater than a 12 months previous.
Lengthy-lived credentials include a big threat of information breaches
Lengthy-lived cloud credentials by no means expire and regularly get leaked in supply code, container photographs, construct logs, and utility artifacts, in keeping with Datadog. Previous analysis carried out by the corporate has proven they’re the most typical reason for publicly documented cloud safety breaches.
SEE: The highest 5 cybersecurity tendencies for 2025
Krug mentioned there may be mature tooling out there to make sure secrets and techniques don’t find yourself in manufacturing environments, similar to static code evaluation. Datadog’s report additionally notes the rise of IMDSv2 enforcement in AWS EC2 situations, an essential safety mechanism to dam credential theft.
There are much less long-lived credentials, however change is simply too gradual
There have been strikes to mitigate the issue, similar to AWS launching IAM Identification Centre, permitting organisations to centrally handle entry to AWS purposes. Whereas corporations are within the course of of adjusting to the service, Krug mentioned, “I just don’t know that everyone considers this their highest priority.”
“It definitely should be, because if we look at the last 10 years of data breaches, the primary theme is that long-lived access key pairs were the root cause of those data breaches combined with overly permissive access,” he defined. “If we eliminate one side of that, we really substantially reduce the risk for the business.”
The long-lived credentials drawback isn’t unique to APAC — it’s a world challenge
Based on Krug, APAC is not any completely different from the remainder of the world. With no regulation to manage the administration of long-lived credentials within the cloud in any specific jurisdiction, corporations worldwide use related approaches with related cloud suppliers, typically throughout a number of world jurisdictions.
Extra Australia protection
What’s stopping the transfer away from long-lived credentials?
The hassle required to transition groups to single sign-on and short-term credentials has slowed the adoption of those practices. Krug mentioned the “lift and shift” concerned in migrating growth workflows to single sign-on could be appreciable. That is partly as a result of mindset shift required and partly as a result of organisations should present satisfactory assist and steerage to assist groups adapt.
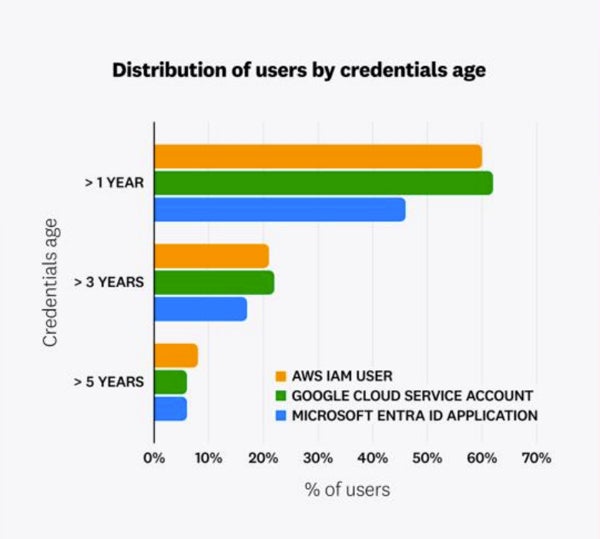 Many cloud credentials are over one 12 months previous. Supply: Datadog
Many cloud credentials are over one 12 months previous. Supply: Datadog
Nevertheless, he famous that instruments like AWS Identification Centre, which has been obtainable for 3 years, have made this transition extra possible. These instruments are designed to scale back developer friction by streamlining the authentication course of, minimising the necessity for repeated MFA sign-ins repeatedly, and guaranteeing that workflows stay environment friendly.
SEE: How AI is amplifying the dangers of information within the cloud
“AWS Identity Centre is a great product and enables these very seamless user flows, but folks are still midstream in migrating to it,” Krug mentioned.
What do you have to do along with your long-lived credentials?
Datadog’s report warned that it’s unrealistic to count on that long-lived credentials could be securely managed. The seller recommends that corporations undertake safe identities with trendy authentication mechanisms, leverage short-lived credentials, and actively monitor modifications to APIs that attackers generally use.
“Organisations should leverage mechanisms that provide time-bound, temporary credentials,” the report mentioned.
Workloads. For workloads, Datadog mentioned this finish could be achieved with IAM roles for EC2 situations or EKS Pod Identification in AWS, Managed Identities in Microsoft Azure, and repair accounts connected to workloads for Google Cloud if the organisation makes use of the main world hyperscalers.
People: For human customers, Datadog mentioned the simplest resolution is to centralise id administration utilizing an answer like AWS IAM Identification Heart, Okta, or Microsoft Entra ID and keep away from utilizing particular person cloud customers for every worker, which it labelled “highly inefficient and risky.”






