AI can now reconstruct speech by concrete utilizing only a laptop computer’s unshielded microphone wiring
Laptop computer mic cables double as antennas, leaking audio by radio harmonics
MEMS microphones emit alerts that betray non-public conversations with none system compromise or malware
A brand new type of eavesdropping makes use of synthetic intelligence to recuperate speech from gadgets by partitions.
Researchers from the College of Florida and Japan’s College of Electro-Communications demonstrated even by a 25 cm concrete barrier, attackers can precisely reconstruct speech utilizing nothing greater than an FM receiver, a copper antenna, and machine studying instruments.
It’s possible you’ll like
So, why laptops?
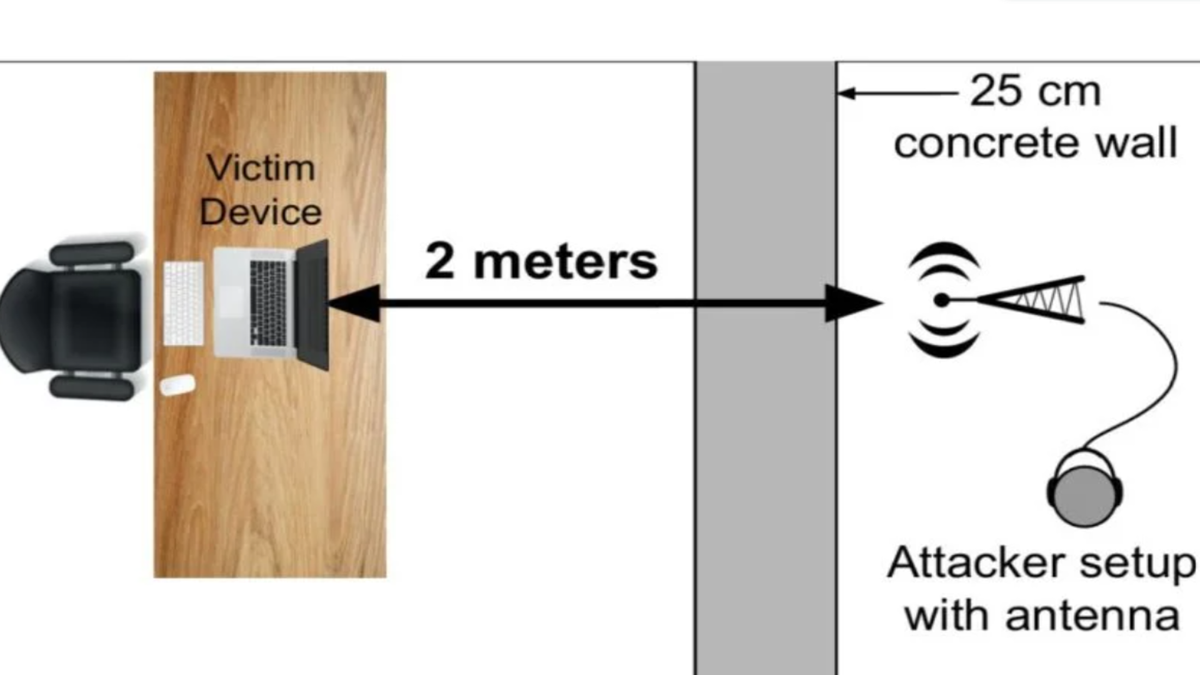
(Picture credit score: eeNews)
The microphones in lots of laptops are linked by way of lengthy, unshielded wires, successfully turning them into antennas, the researchers observe.
“With an FM radio receiver and a copper antenna, you can eavesdrop on these microphones. That’s how easy this can be…It costs maybe a hundred dollars, or even less,” stated Prof. Sara Rampazzi on the College of Florida.
The analysis revealed an accuracy of as much as 94.2% in recognizing spoken digits, whereas OpenAI’s generative fashions achieved a transcription error fee as little as 6.5%.
The researchers examined a number of MEMS microphones, together with the MP34DT01-M from STMicroelectronics, Knowles SPM0405 (now Synaptics), TDK InvenSense CS-41350 and T3902, and Vesper’s VM3000 (now a part of Qualcomm).
These microphones emit electromagnetic alerts that may leak acoustic information by radio harmonics.
In line with STMicroelectronics, “this is an intrinsic behavior of Digital PDM MEMS microphones,” and the design utilized in laptops usually lacks shielding, turning flat cables into very best antennas.
To mitigate this threat, specialists suggest relocating microphones inside laptops to scale back cable size and shielding the wires. Additionally they suggest utilizing unfold spectrum clocking to scale back the intelligibility of emissions with out affecting efficiency.
These fixes are comparatively easy, however they’re related for newer gadgets shifting ahead. What about pre-existing gadgets, then?
Common customers have to spend money on one of the best antivirus or endpoint safety options, which supply some safety despite the fact that they aren’t explicitly listed to defend in opposition to this new risk.
These instruments usually function on the software program degree and should not detect passive assaults that don’t contain code execution or system compromise.
For people looking for one of the best identification theft safety, this analysis exhibits that even conversations assumed to be non-public could also be inside attain of refined, low-cost surveillance.
You may also like






